
Decipher 10 No-Logs VPNs Policies & Practices [Free & Paid]
Our online activities are constantly tracked by ISPs, potential hackers, and even by the VPNs we buy for privacy. The truth is, some VPN proactively log user data to sell, while others are forced to and must hand it over to the government upon request. While VPN providers use “no-logs policy” as a selling point, is it truly trustworthy?

Follow SafePaper as we decipher the truth behind VPN logging policies and their actual practices. Find out genuine no-logs VPNs that take your privacy seriously, whether you pay for it or not.
Table of Contents
What Are VPN Logs? Necessary Data vs. Identifying Data
VPN logs are information recorded by a VPN service during operation. There are basically no zero-log VPNs because a VPN requires necessary data to function. The clutch is whether the logs can be linked to who you are.
| Necessary Data | Identifying Data |
| Aggregated bandwidth usage | Your real IP address |
| Total number of server connections | VPN server IP address you connect to |
| Server crash reports | Websites you visit |
| Operating system logs | Applications you use |
| Concurrent account connections | DNS queries |
| Abuse and fraud prevention data | VPN servers used |
| Network type | Files downloaded |
| Device operating system version | Device identifier |
| … | … |
In addition to the above information, VPN providers also need to collect your email and billing information for payment. The permission for virtual mail address registration and support for cryptocurrency payments increases user privacy.
What Makes a No-Logs VPN Trusted?
The nature of a no-logs policy is actually a self-declaration, any VPN service provider can say they follow a strict no-logs policy on their website. So, how do we determine whether a claim is trustworthy? The following practices add credibility.
1. Clear & Transparent Privacy Policy
A clear and transparent privacy policy is fundamental. A trusted VPN provider should clearly outline in its policy what data it collects and how it is used. While policies may seem intimidating in this way, in reality, the more specific and detailed they are, the better. A Privacy Policy can usually be found in the footer section of a website.
2. Technical Approaches Like RAM-Only Servers
A trustworthy VPN provider should also implement various technical measures to handle user data. It would be better if the provider had a dedicated webpage explaining how they operate. Typical technical measures to protect user data are:
- RAM-Only Server: RAM-only servers operate entirely in memory, and all data will be automatically wiped clean each reboot. This physically prevented long-term logging.
- Zero Trust Network Access (ZTNA): Zero Trust Network Access (ZTNA) is a security model that “never trust, always verify.” It constantly verifies who’s accessing and guarantees least privilege access.
- Private DNS: When using a third-party public DNS, your DNS queries may also be logged by the third party. Therefore, trustworthy VPNs use their own private DNS to better protect user privacy.
3. Transparency Report with 0 Disclosure
A transparency report clearly shows how many times a VPN provider has been asked to hand over user data by governments or courts, and how they respond. A consistent record of zero verifies that their no-logs system is effective.
4. Third-Party Independent Audit
Many VPN service providers are hiring an external cybersecurity firm to conduct an independent audit, which can cover application security, protocol security, VPN infrastructure, etc. Regarding the “no-logs” issue, terms we should look for are “Privacy Audit”, “No-Logs Audit”, or something like that.
During this audit, security experts conduct an in-depth examination of the VPN service provider’s servers, code, and backend systems to confirm that their data handling practices fully comply with their “no-logs” statement.
💡 To be noticed, an audit is not a get-out-of-jail-free card. It only proves that the no-logs policy was effective on the sample servers in the past, normally the past year. It cannot promise anything about the future.
5. Privacy-Friendly Jurisdiction
Many countries have strict laws requiring companies to store user data. For this reason, reliable no-logs VPNs often operate outside of jurisdictions with data retention laws. Typical examples of unfriendly jurisdictions include:
🧑⚖️ Countries with Data Retention Laws
Countries like the UK, Germany, France, Australia, and many other EU member states have laws that force VPN providers to collect and store user data for access by law enforcement.
👀 Intelligence-Sharing Alliances
Member states of these alliances are obliged to share user data obtained through companies. Even if a member does not wish to record data, they are subject to laws that can compel them to secretly monitor and share user data.
- Five Eyes: US, UK, Canada, Australia, and New Zealand.
- Nine Eyes: Five Eyes countries plus Denmark, France, the Netherlands, and Norway.
- Fourteen Eyes: Nine Eyes countries plus Germany, Belgium, Italy, Spain, and Sweden.
🌍 Other Countries with Unique Data Control Laws
Countries like India, Russia, Turkey, the UAE, and mainland China have unique and extremely strict data localization or surveillance laws, making operating a truly “no-logs” VPN impossible. For example, CERT-In 2022 directives require VPNs to retain logs/user information, after which a large number of VPN providers withdrew from Indian physical servers.
The technology of virtual servers was born out of necessity. That is to say, the server is physically located in a secure country, like Singapore, but with an IP address in the Indian network segment.
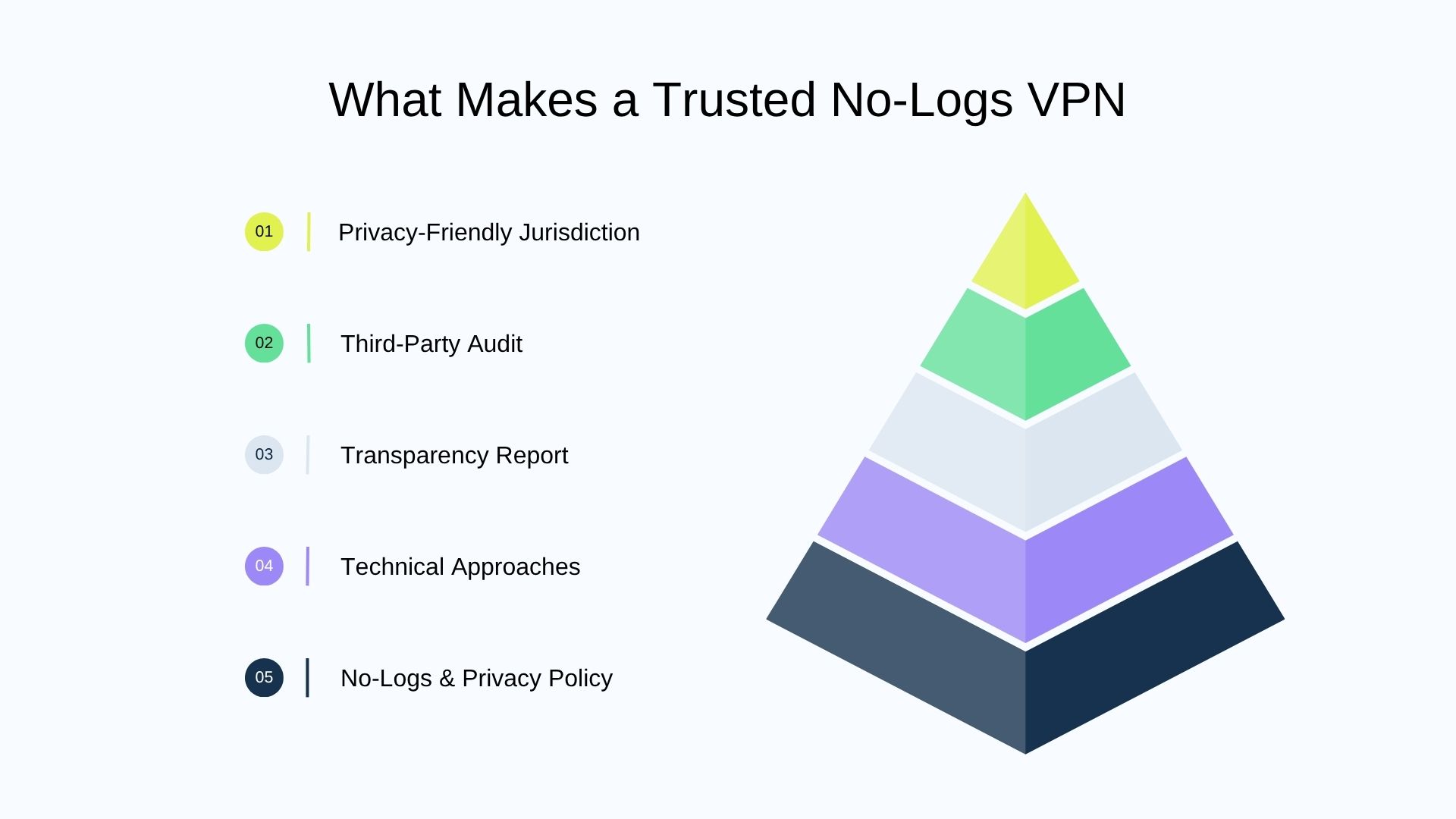
So, which of the 5 factors carries the most weight? Jurisdiction trumps everything. No-logs and privacy policy are self-declarations; technical approaches and transparency report add credibility to them. Third-party audit proves their policies are effective only during the audit period. However, all of the above is meaningless if the provider is located in the jurisdiction, for the governments can secretly ask for user data even without being noticed by an audit, and any current promise can be compelled to change in the future.
Decipher 5 Premium VPN Logging Policies & Practices
Based on the above conclusion, we dive deep into 5 premium VPNs that claim no-logs and offer no free version. Let’s see whether they deserve the pay.
1. Mullvad VPN

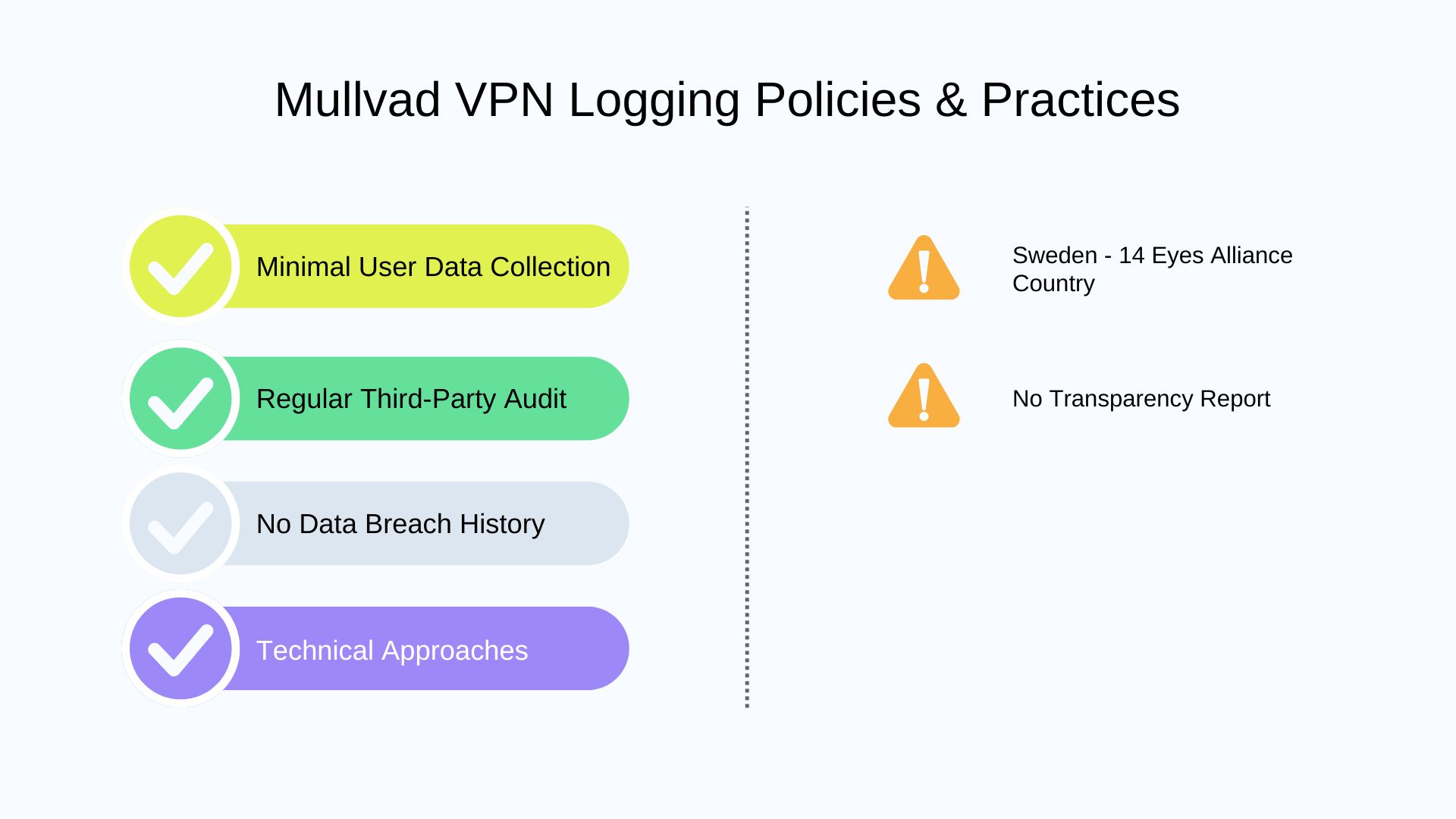
📋 No-Logs & Privacy Policy
Mullvad VPN follows a minimal data retention policy. Log in with an anonymous number, and no personal data is required. They only collect aggregated application data, generic system metrics, and total simultaneous connections. Logs they never collect are:
❌ User traffic
❌ DNS requests
❌ Connections, disconnects, timestamps
❌ IP addresses
❌ User bandwidth
❌ Account activity
⚒️ Technical Approaches
Mullvad VPN uses RAM-only servers and private DNS to protect user data. Its DNS Leak Protection was also tested by Cure53 in 2020.
📃 Transparency Report
Mullvad doesn’t publish regular transparency reports like some of its competitors. They believe this report is also a self-declaration and can not be verified. Instead, it has proven its no-logs policy through real-world testing. In 2023, Swedish police raided Mullvad’s office but found nothing on the servers.
👩⚖️ Third-Party Audit
Mullvad VPN clearly lists all the audits they’ve conducted on their blog section. Most are app-security related. In terms of user data, the following infrastructure audits are conducted.
| From | To | Audited by |
| 2024-06-03 | 2024-06-14 | Cure53 |
| 2023-05-08 | 2023-05-26 | Radically Open Security (RoS) |
| 2022-04-25 | 2022-05-13 | Assured AB |
| 2020-11 | 2020-12 | Cure53 |
🌎 Jurisdiction
Mullvad VPN is based in Sweden, a member of the 14 Eyes alliance, which is worrying. However, the 2023 real-world test proved the effectiveness of its no-logs system even within Sweden’s jurisdiction. Mullvad also takes a strong stance in terms of servers in sensitive regions. It directly removes their servers in places like India to protect user data.
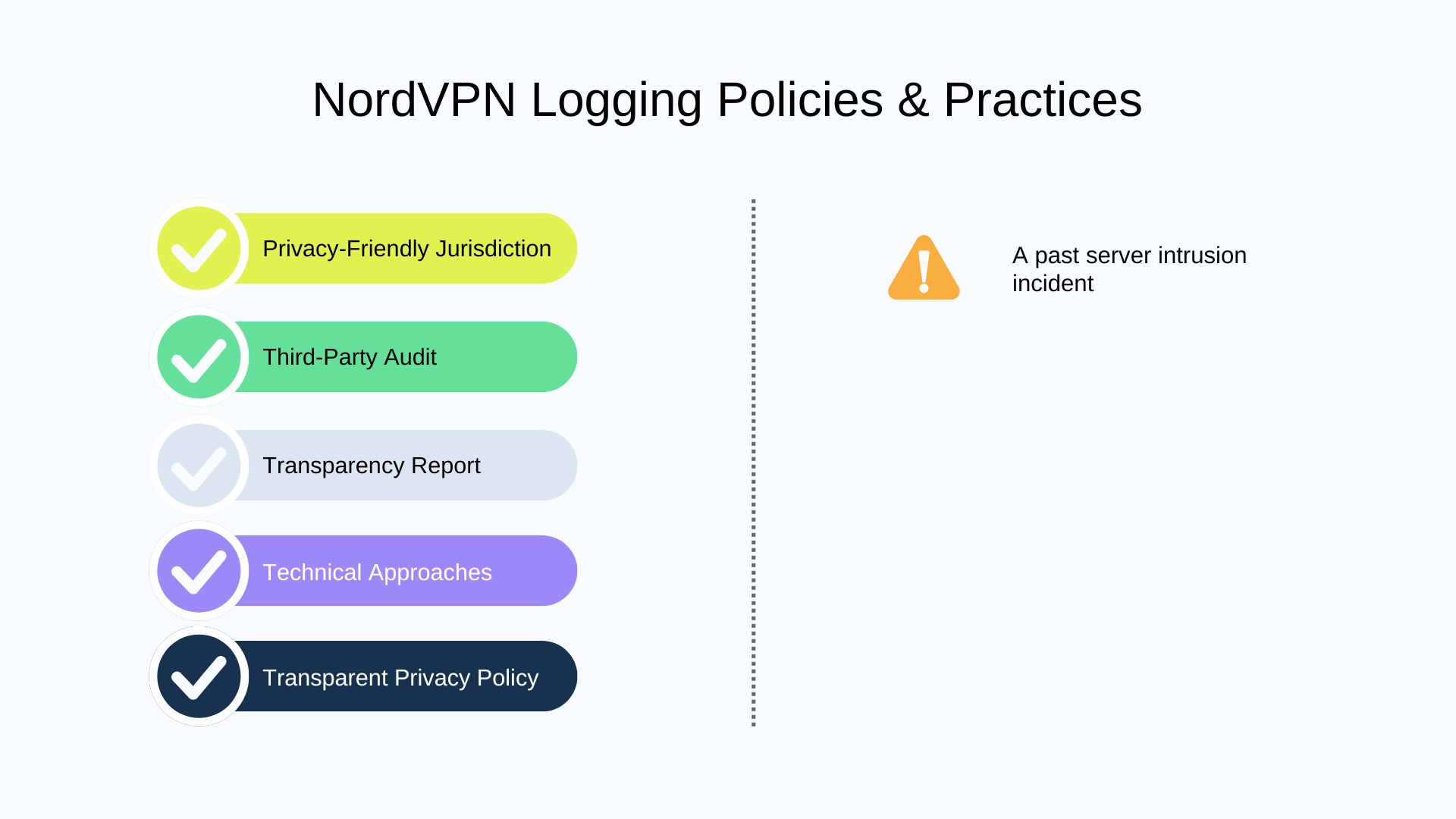
2. NordVPN

📋 No-Logs & Privacy Policy
NordVPN also clearly lists their logs and things never logged on their privacy policy page. Compared to other providers, NordVPN made this more transparent, even for the data collected. Some are collected only for a dedicated feature.
| Will Collect | Not Collect |
| Server load (CPU, RAM) | Browsing data |
| Username & last session timestamp (deleted in 15 mins) | Traffic logs |
| Whether service was used in the last 30 days | Used bandwidth |
| Interaction data | Real IP address |
| n-app events & device info (anonymous, can opt-out) | Connection timestamp |
| Threat Protection data | |
| Meshnet only: hashed device ID, email, file transfer stats. | |
| Dedicated IP only: Links your email to the IP address. | |
| Smart DNS only: Stores your real IP address |
We do not think this is excessive. Instead, we always encourage more transparency, especially on the data that will be collected.
⚒️ Technical Approaches
Technically, it utilizes RAM-only servers and private DNS. Besides, there are bug bounties programs to build user trust.
📃 Transparency Report
NordVPN frequently updates its transparency report about how many requests it receives from DMCA and government institutions. No user data disclosed.
NordVPN indeed experienced a data breach in 2018, when one server rented from a Finnish data center was compromised. Fortunately, no user data was compromised, and they immediately terminated the contract and switched from rented servers to a private model.
👩⚖️ Third-Party Audit
The following are all third-party independent audits NordVPN has conducted for its no-logs policy. This table excludes audits that only involve client-side application or protocol security testing.
| From | To | Audited by |
| 2024-11-18 | 2024-12-20 | Deloitte |
| 2023-11-30 | 2023-12-07 | Deloitte |
| 2022-11-21 | 2022-12-10 | Deloitte |
| 2020-05-20 | 2020-05-28 | PwC AG |
| 2018 | 2018-11 | PwC AG |
🌎 Jurisdiction
NordVPN operates from Panama, which is not a member of the “Five Eyes/Nine Eyes/Fourteen Eyes” intelligence-sharing alliance, and doesn’t mandate data retention. For compliance and user needs, NordVPN uses virtual server solutions in some sensitive jurisdictions such as India, Afghanistan, Egypt, etc.
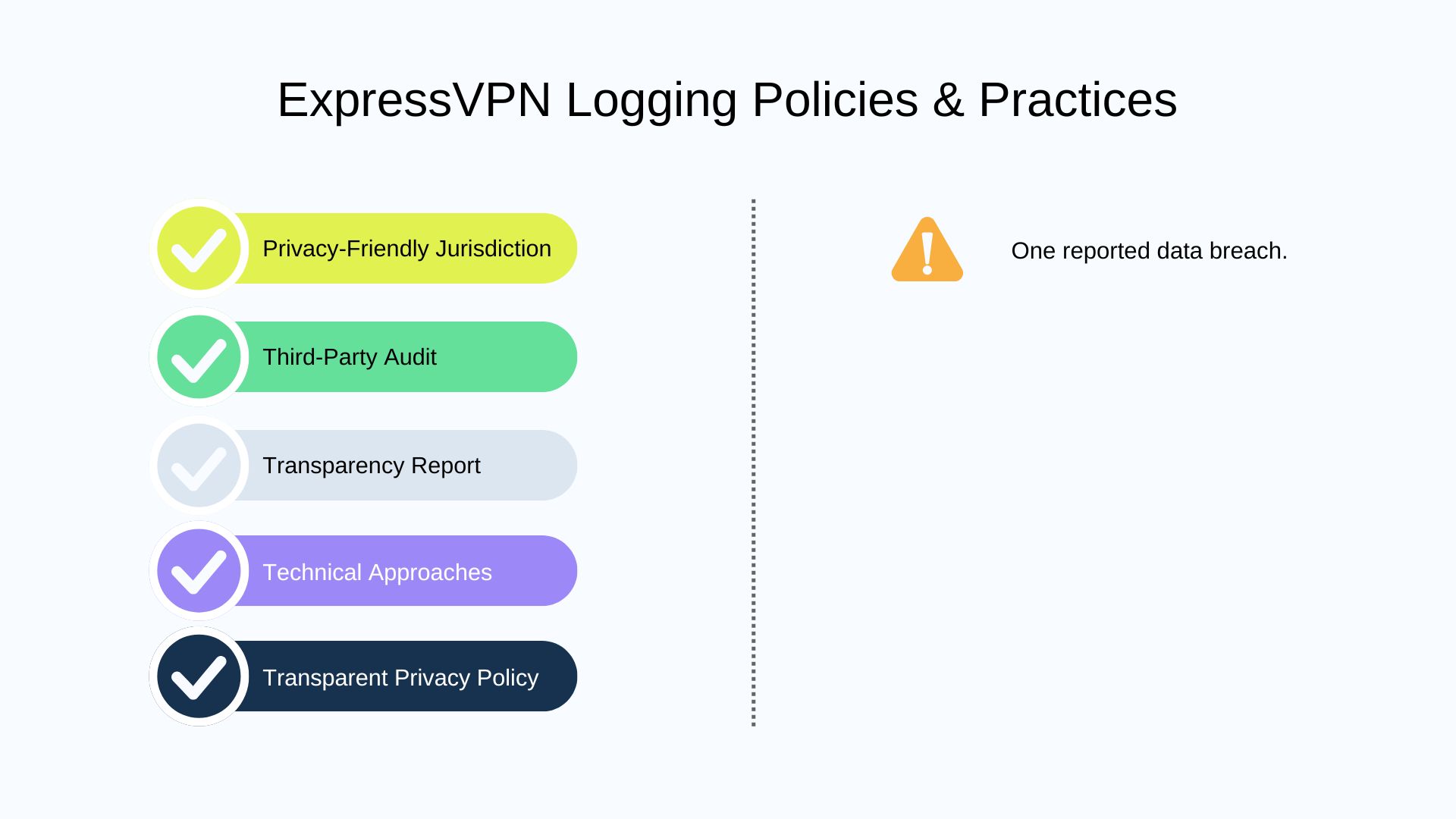
3. Express VPN

📋 No-Logs & Privacy Policy
In the privacy policy page, ExpressVPN also discloses what it collects and what they don’t collect clearly. Most are necessary for business operations or are actively selected and controlled by users.
| Will Collect | Not Collect |
| Aggregate Stats | Browsing history |
| MediaStreamer IPs | Traffic content or destinations |
| Account Info | DNS queries |
| Data added to ExpressVPN Keys | Original IP addresses |
| App Diagnostic Data | Any VPN connection timestamps |
| Data for marketing purposes | Session logs |
| Identity Defender data |
⚒️ Technical Approaches
ExpressVPN is a pioneer in RAM-only server technology. It also uses its own private, encrypted DNS on each server to prevent data leaks.
📃 Transparency Report
Every six months, ExpressVPN publishes a transparency report detailing the legal requests it received and how it responds. For sure, no user data disclosed.
There is one notable ExpressVPN data breach news related to ExpressVPN. CNET reporter Attila Tomaschek discovered that there was a bug in the split tunneling feature of its past Windows client version, which caused some DNS requests to be leaked to the user’s ISP’s DNS server instead of being sent through ExpressVPN’s encrypted server, allowing the ISP to see the domain names visited by the user.
👩⚖️ Third-Party Audit
ExpressVPN undergoes regular independent audits to verify its privacy and security.
| From | To | Audited by |
| 2024-12 | 2025-02 | KPMG LLP |
| 2023-10 | 2023-12 | KPMG LLP |
| 2022-06 | 2022-09 | KPMG LLP |
| 2019-05 | 2019-06 | PwC AG |
🌎 Jurisdiction
ExpressVPN is headquartered in the British Virgin Islands, which has no data retention laws and is not part of the Five Eyes/Nine Eyes/Fourteen Eyes intelligence-sharing alliances. To address restrictive data laws, ExpressVPN used virtual servers for India in 2022, while physically hosting these servers in Singapore and the UK.
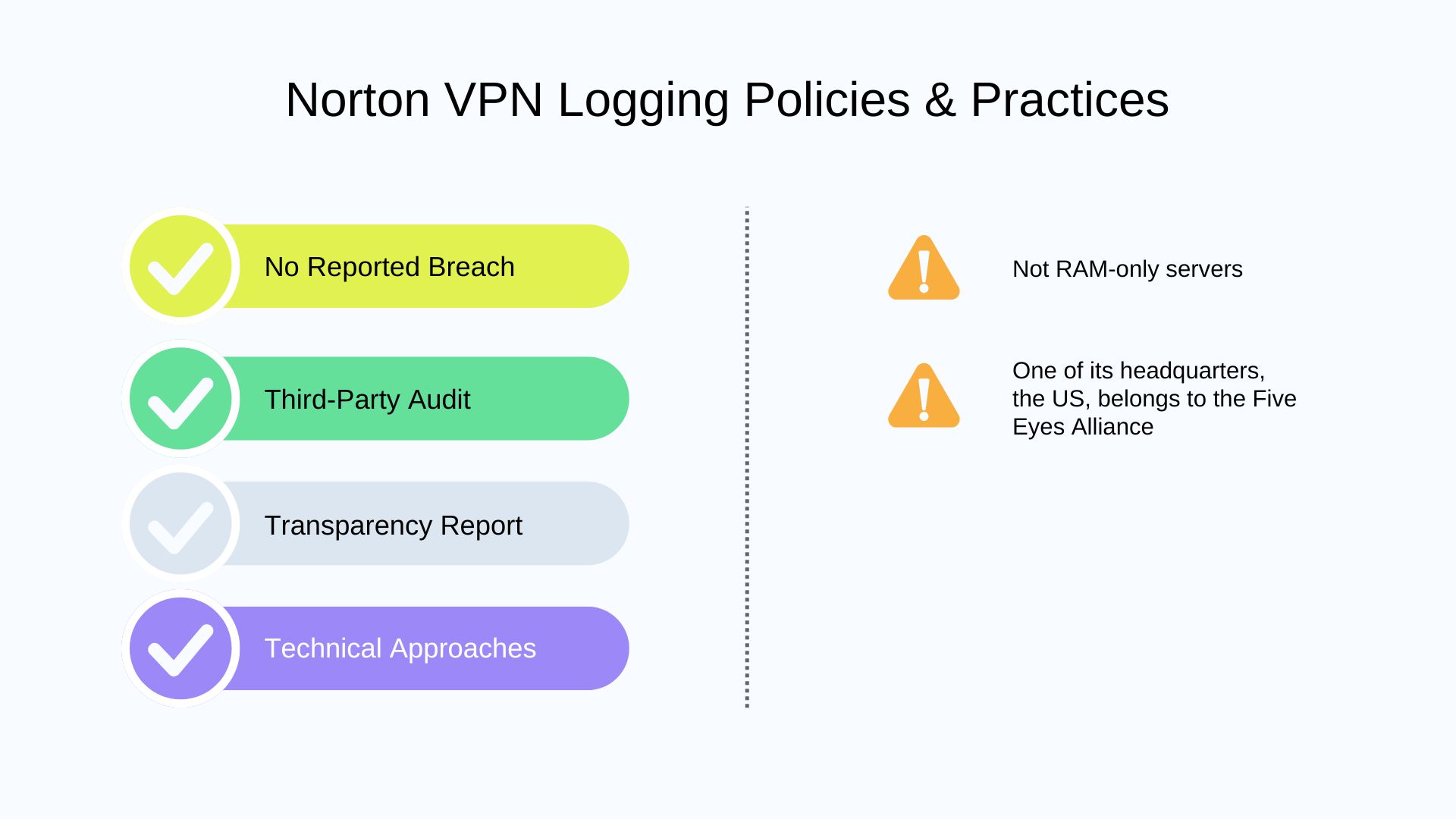
4. Norton VPN

📋 No-Logs & Privacy Policy
Below is the information listed in the VPN section of Norton’s privacy policy page.
| Will Collect | Not Collect |
| Connection events | Browsing history |
| App events | Traffic destination |
| User-submitted crash reports | Device IP address |
| Aggregate data transferred | Session duration |
| Account data | DNS queries |
⚒️ Technical Approaches
Norton VPN does not use RAM-Only servers, but uses its own private DNS servers.
📃 Transparency Report
Norton VPN publishes a transparency report every quarter detailing government data requests and states that no user data is provided.
Though other products from Norton, like Norton LifeLock, have experienced some security incidents, there have been no incidents reported related to the VPN service.
👩⚖️ Third-Party Audit
| From | To | Audited by |
| 2025-06-09 | 2025-08-26 | VerSprite |
| 2024-02-21 | 2025-08-27 | VerSprite |
🌎 Jurisdiction
Norton VPN is owned by Gen Digital, which is headquartered in the USA, and has dual headquarters in the Czech Republic. The United States is a member of the “Five Eyes” intelligence alliance, while the Czech Republic is part of the European Union and is not a member of any of the alliances. As for sensitive regions, Norton VPN removed Indian servers, but uses virtual servers in Russia for some app versions.
There’s another similar provider named Bitdefender that offers a full security suite, including a VPN service. Check our Bitdefender VPN review for more details.
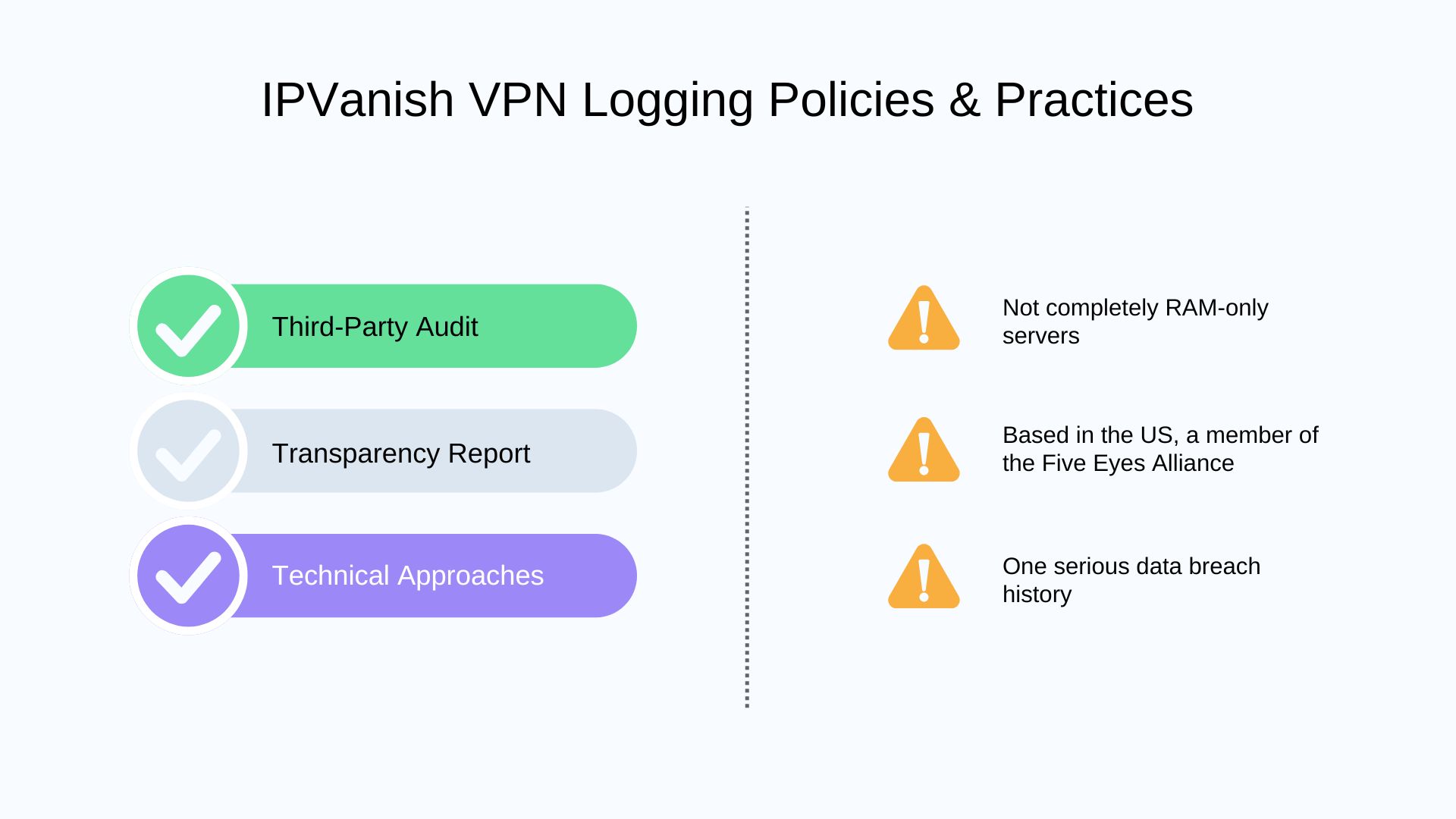
5. IPVanish VPN

📋 No-Logs & Privacy Policy
| Will Collect | Not Collect |
| Account Information (name, address, email, etc.) | Browsing history |
| Transaction Information | when connected to the VPN service |
| Site usage information and app data | IP address |
| Contact information | connection time stamps |
| Subscription | DNS inquiries |
⚒️ Technical Approaches
As of 2025, IPVanish has launched RAM-only servers in the first 19 cities, and plans to migrate all 148 server locations to RAM-only architecture by 2027. Besides, IPVanish provides private DNS services.
📃 Transparency Report
IPVanish VPN quarterly publishes a transparency report, which indicates no user data disclosure from October 2024 to September 2025.
IPVanish was the subject of a serious user data disclosure in 2016. Claimed no-logs, IPVanish cooperated with a criminal investigation led by the U.S. Department of Homeland Security, providing law enforcement with connection log information from a specific user. After IPVanish was acquired by its new parent company in 2017, no such incident has been reported yet.
👩⚖️ Third-Party Audit
| From | To | Audited by |
| 2022 | 2022-03 | Leviathan Security Group |
| 2024 | 2025-02-21 | Schellman Compliance, LLC |
🌎 Jurisdiction
IPVanish is headquartered in New York, USA. Although the US does not have mandatory data retention requirements for VPN services, it is one of the countries in the “Five Eyes” intelligence alliance.
You might notice that our analysis of paid VPNs doesn’t include big names like Surfshark and CyberGhost. This is because these brands have close VPN relationships with NordVPN and ExpressVPN, and they likely follow similar logging practices.
Decipher 5 Free VPN Logging Policies & Practices
Are there free no-logs VPNs? Yes, there are. The following report covers 5 free VPN providers, some of which offer unlimited data, while others have data caps. Let’s find out if all free VPNs are as dangerous as advertised.
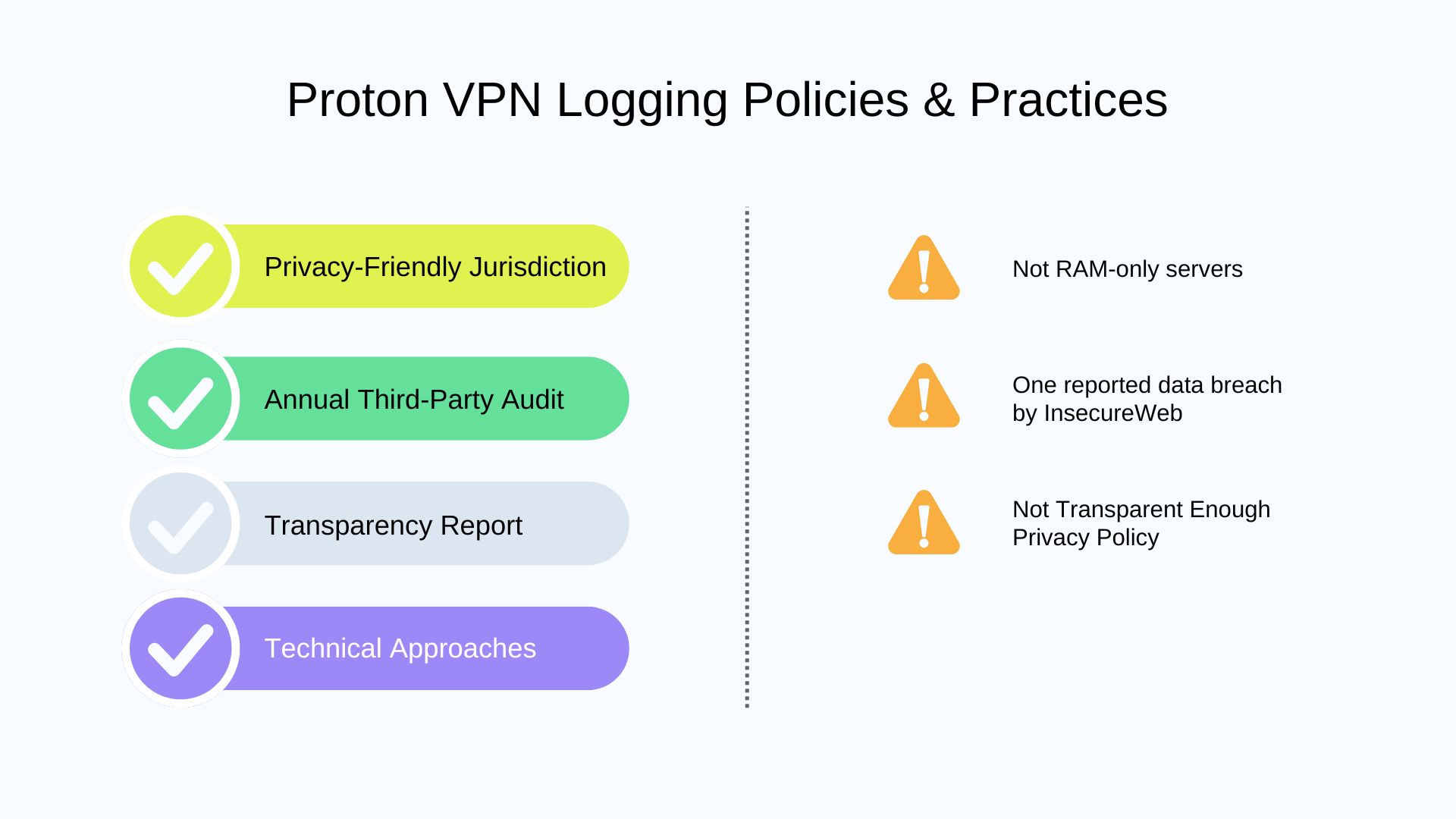
1. Proton VPN

📋 No-Logs & Privacy Policy
Proton VPN doesn’t list the information it collects in its privacy policy page. Given the relationship between this VPN product and its parent company, Proton, you may find more details about the information it collects on Proton’s privacy policy page. Here’s what they claim never collect:
❌ IP addresses or location
❌ Web pages you visited
❌ Connection logs
❌ Session lengths
❌ Users’ traffic
⚒️ Technical Approaches
Proton VPN does not use RAM-only servers. They use fully encrypted disk storage. They believe it will be just as effective as RAM-only servers. Proton VPN uses its own private DNS to handle all DNS queries to avoid leaks from third-party resolvers.
📃 Transparency Report
Proton VPN regularly updates its transparency report on the law enforcement requests it receives and rejects. The report shows that as of June 2025, all requests had been denied.
Proton VPN has no known security data breach history, except for the one reported by InsecureWeb in 2023. It reported that a hacker named Ninja Defender successfully gained unauthorized access to about 105Kb of ProtonVPN user email data.
👩⚖️ Third-Party Audit
Proton VPN’s no-logs policy is audited annually. As of 2025, it has passed its fourth audit. Besides, Proton open-sourced its VPN app code in 2020, allowing for inspection by the wider security community.
| From | To | Audited by |
| 18.08.2025 | 19.09.2025 | Securitum |
| 03.07.2024 | 12.07.2024 | Securitum |
| 24.04.2023 | 01.05.2023 | Securitum |
| 21.02.2022 | 24.03.2022 | Securitum |
🌎 Jurisdiction
Proton VPN is located in Switzerland, a country with no mandatory data retention requirements and known for having strong privacy laws. Furthermore, Switzerland is not a member of any “Eyes” intelligence alliance. As for servers in sensitive regions, it removed all physical servers in India since 2022 and switched to virtual servers located in privacy-friendly countries, but still offers Indian IP addresses.
2. X-VPN

📋 No-Logs & Privacy Policy
| Will Collect | Not Collect |
| Certain device system information | User IP address |
| Country-level location | Server IP address user connect to |
| Email(optional) | Browsing history |
| Simultaneous login number | data content |
| Connection and diagnostics data | DNS queries |
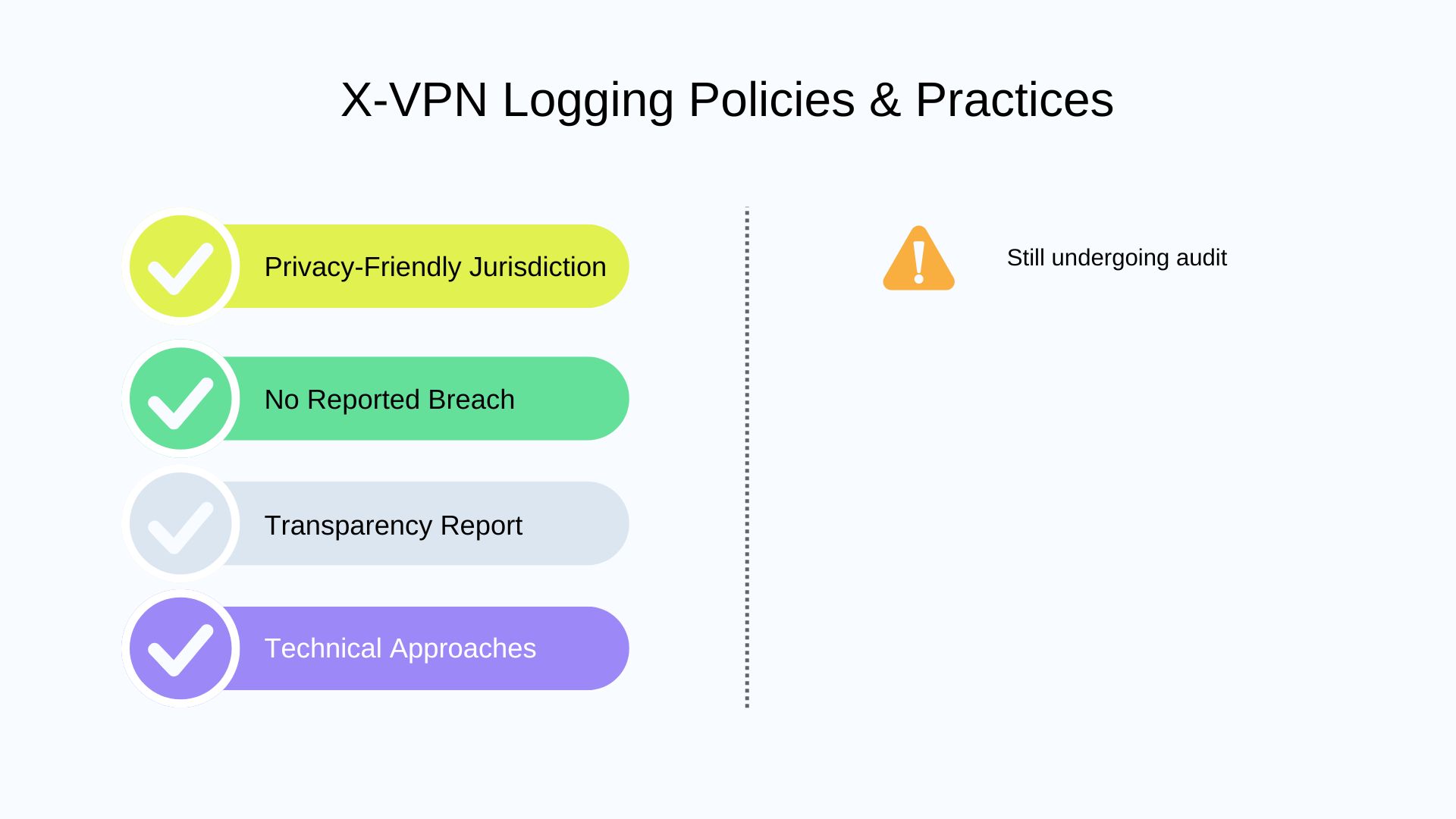
⚒️ Technical Approaches
X-VPN fully deploys RAM-only servers and private DNS to maximize user privacy. We also noted that their Trust Center page explains their efforts in the tech layer, utilizing technologies like zero-trust control and buy bounty programs.
📃 Transparency Report
X-VPN publishes its transparency report on the Trust Center page, explaining in detail how it protects user data technically and procedurally.
There’s no data breach incident related to X-VPN reported, which is quite reassuring, especially as a VPN offers an unlimited free version.
👩⚖️ Third-Party Audit
There are currently no third-party audit reports on its no-logging policy, mainly because this VPN service is relatively new compared to the aforementioned big names. However, according to a CIO report, X-VPN is undergoing its first third-party independent audit now.
🌎 Jurisdiction
X-VPN is part of Lightninglink Networks Pte. Ltd., a Singaporean cybersecurity company. Singapore has no data retention laws, and the company is not a member of the 5/9/14 Eyes alliances.
3. Hide.me VPN

📋 No-Logs & Privacy Policy
| Will Collect | Not Collect |
| Email address | VPN sessions |
| Website usage data | IP address or physical address |
| Timing, frequency and patterns of website visit | Websites you visit |
| Browsing behaviour | |
| Activity related to VPN connection | |
| VPN connection logs and timestamps |
⚒️ Technical Approaches
Hide.me fully upgraded its infrastructure in 2020 to run on RAM-only servers for maximum privacy. It also operates private DNS servers on all its VPN endpoints.
📃 Transparency Report
Hide.me has published a transparency report on its website since 2013 (available as a PDF document), with the last update being in 2024. No user data disclosure, and no reported data breach incident.
👩⚖️ Third-Party Audit
| From | To | Audited by |
| 03.09.2024 | 06.06.2024 | Securitum |
| 2015 | 2015 | DefenseCode |
🌎 Jurisdiction
Hide.me is based in Malaysia, a country that is not part of any major intelligence-sharing alliances and has no data retention requirements for VPNs.
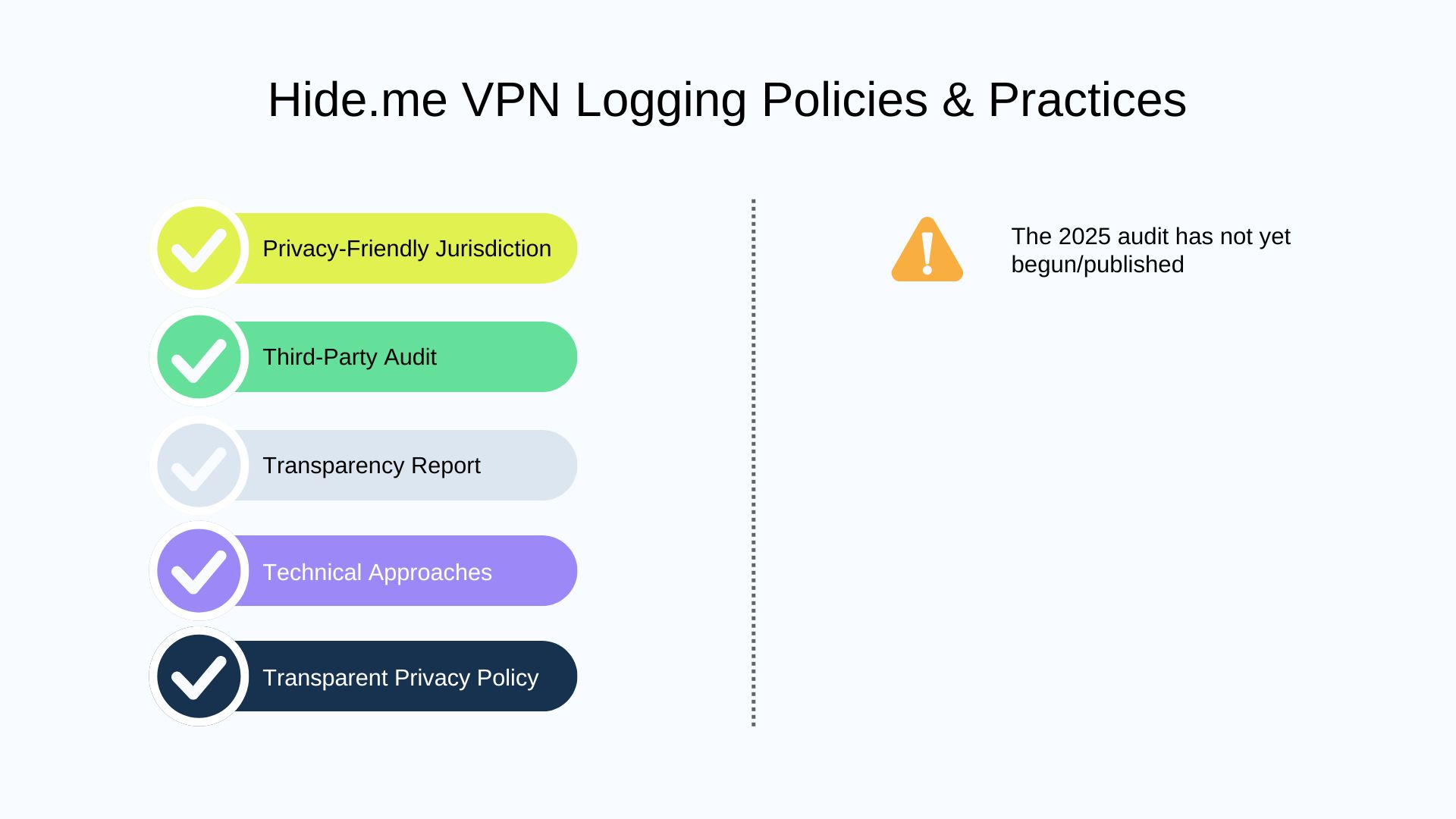
To be fair, the notification section isn’t really a notification at all, as many other VPNs’ audits are also stuck in 2024.
4. TunnelBear

📋 No-Logs & Privacy Policy
| Will Collect | Not Collect |
| Account User Data | IP addresses visiting our website |
| Operational Data | IP addresses upon service connection |
| payment data | DNS Queries while connected |
| VPN connection activities |
⚒️ Technical Approaches
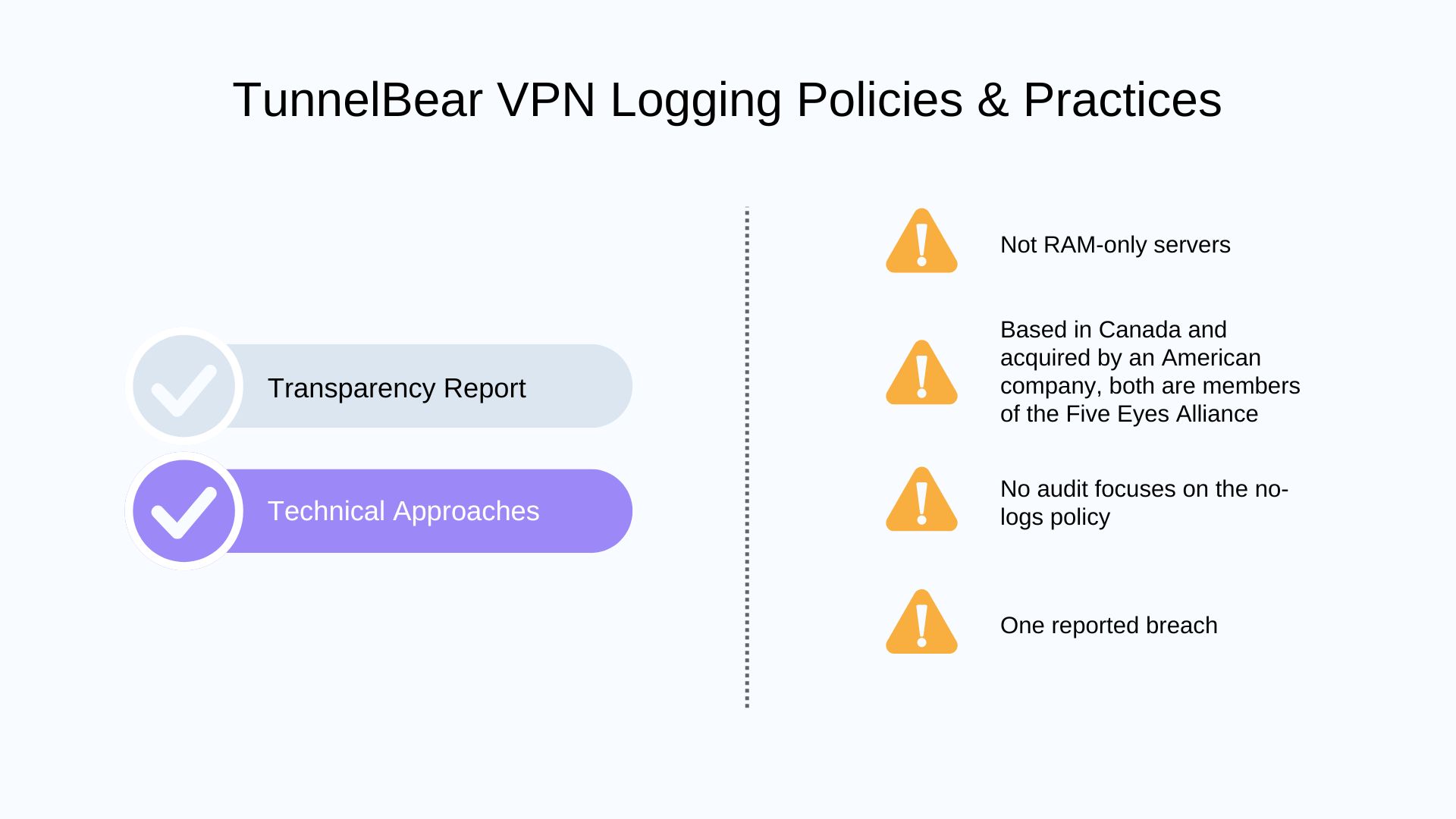
While TunnelBear has used its own DNS servers since 2017 to prevent DNS leaks, it doesn’t use RAM-only servers like its competitors.
📃 Transparency Report
TunnelBear publishes a transparency report every year. However, the latest update is still stuck in 2023, which is quite outdated compared to other providers.
Again, InsecureWeb reported a security breach related to TunnelBear in 2023. It claimed that 13.5 KB of data was stolen, including sensitive user data like emails.
👩⚖️ Third-Party Audit
TunnelBear has been known for undergoing third-party audits since 2016. However, these audits focus on application security rather than its no-logs policy.
We carefully reviewed its audit reports from recent years and found no relevant findings regarding data retention. This means that even though TunnelBear claims to have a no-logs policy, there is currently no audit report to support this.
🌎 Jurisdiction
TunnelBear is headquartered in Canada, a member of the Five Eyes Alliance. Since 2018, TunnelBear has been acquired by McAfee, a company located in the US, which is also a member of the Five Eyes Alliance.
5. Windscribe

📋 No-Logs & Privacy Policy
| Will Collect | Not Collect |
| Total amount of bytes transferred | Sites you visited |
| Timestamp of your last activity | Historical record of VPN sessions |
| Number of parallel connections | Source IP |
| total number of bytes downloaded/uploaded | Anything not mentioned here |
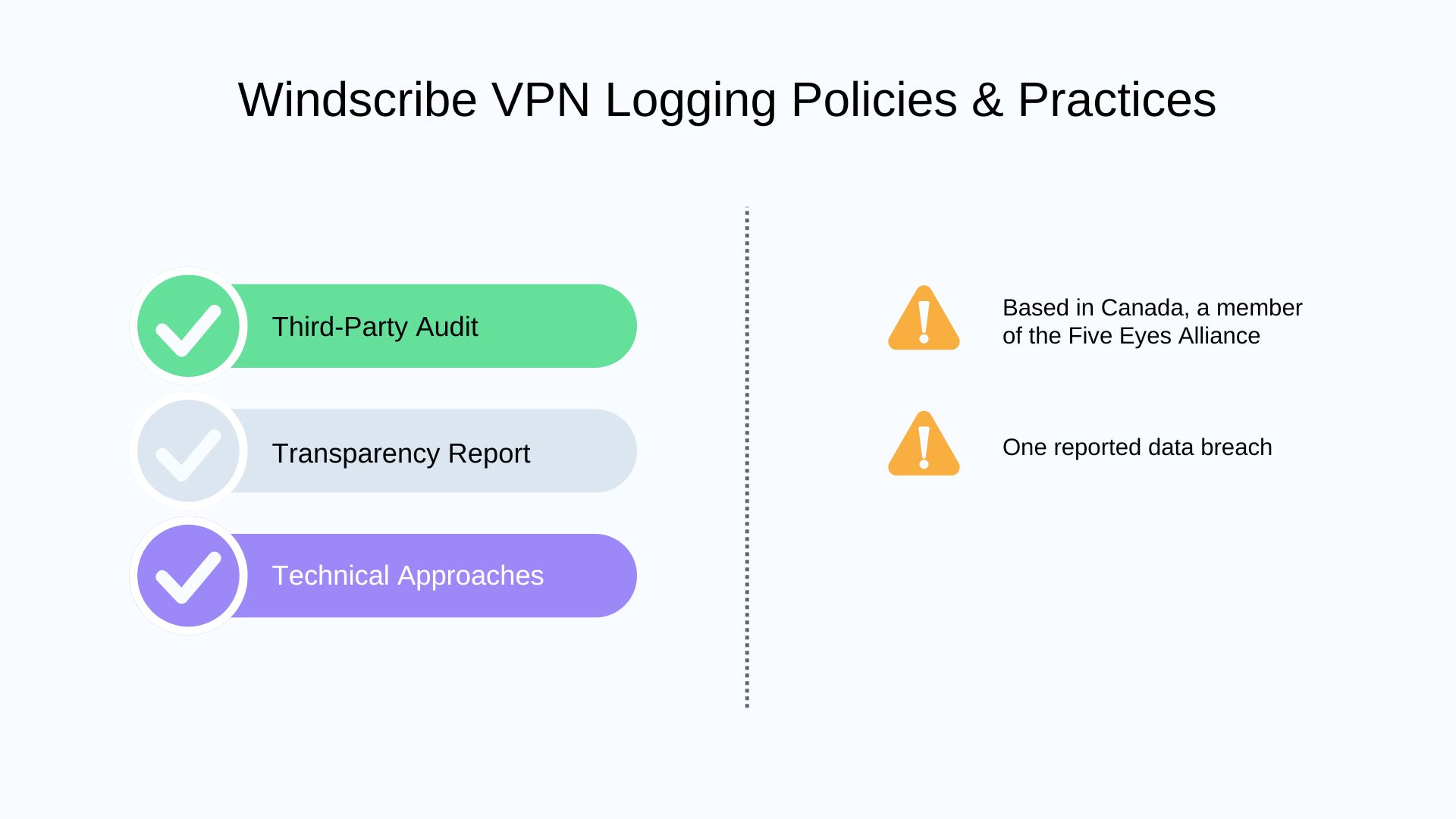
⚒️ Technical Approaches
Windscribe implemented RAM-only servers across its entire network in 2021. Besides, it runs its own private DNS resolver on each VPN server.
📃 Transparency Report
Windscribe updates the DMCA and law enforcement requests it receives on a semi-annual basis in the form of charts on its official website.
Windscribe experienced a data breach incident in 2021 on its Ukrainian servers. The unencrypted servers put user data at risk. After that, it changed all its servers to RAM-Only infrastructure.
👩⚖️ Third-Party Audit
| From | To | Audited by |
| 2024-06 | 2024-06 | Packetlabs |
| 2022-11 | 2022-12 | Cure53 |
🌎 Jurisdiction
Windscribe is headquartered in Canada, which doesn’t have mandatory VPN logging laws, but is a member of the Five Eyes intelligence alliance.
Conclusion
Instead of taking the self-declared no-logs policy easily, it’s better to assess the VPN’s credibility from a series of verifiable actions. SafePaper dives deep into 10 claimed “no-logs VPNs” regardless of their prices, so you can make a choice based on evidence rather than empty promises.
FAQs
How Do I Know If a VPN Is Truly No-Log?
To determine whether a VPN is truly “no-logs,” it is necessary to consider factors like jurisdiction, third-party independent audit, transparency report, technical solutions, and a transparent privacy policy comprehensively, among which jurisdiction is a crucial factor.
Are Paid VPN Safer than Free VPN?
Not necessarily. As we researched above, even paid VPNs can have security vulnerabilities, and there are still reliable free options. The clutch is to carefully examine their policies and practices, rather than simply judging them by “free” or “paid”.
What Is Canary Campaign?
Warrant canaries are a common transparency tool used by VPN providers. They periodically post an “all is well” statement. If they come under government surveillance or a gag order, they may stop updating this statement, indirectly letting users know what’s happening.




