
Is NordVPN Safe? Honest Analysis in 2026
In an age where even a single post can be traced back to your real address, protecting online privacy is no longer an anxiety for geeks, but a basic need for everyone. As a prominent player in the VPN world, NordVPN has naturally become a frequent topic when discussing security, and it claims to offer the industry’s top-notch protection, which sounds almost flawless.
But the question is: is NordVPN safe? As a reviewer devoted to empirical testing, I’m going to take a closer look at NordVPN’s technical foundation, security features, and privacy policy, helping you to decide if it’s the right surfing guardian for you.
Table of Contents
The Ways NordVPN Protects Your Security
To assess how secure NordVPN is, we have to find out what hardcore measures it uses to protect our data. During the two-day test, I installed NordVPN on two of my favorite devices, a MacBook Pro and an iPhone 16 Pro, and experienced its features.
Combining the information on the official website with my personal feelings, here’s a detailed breakdown of its core security mechanisms.
VPN Encryption
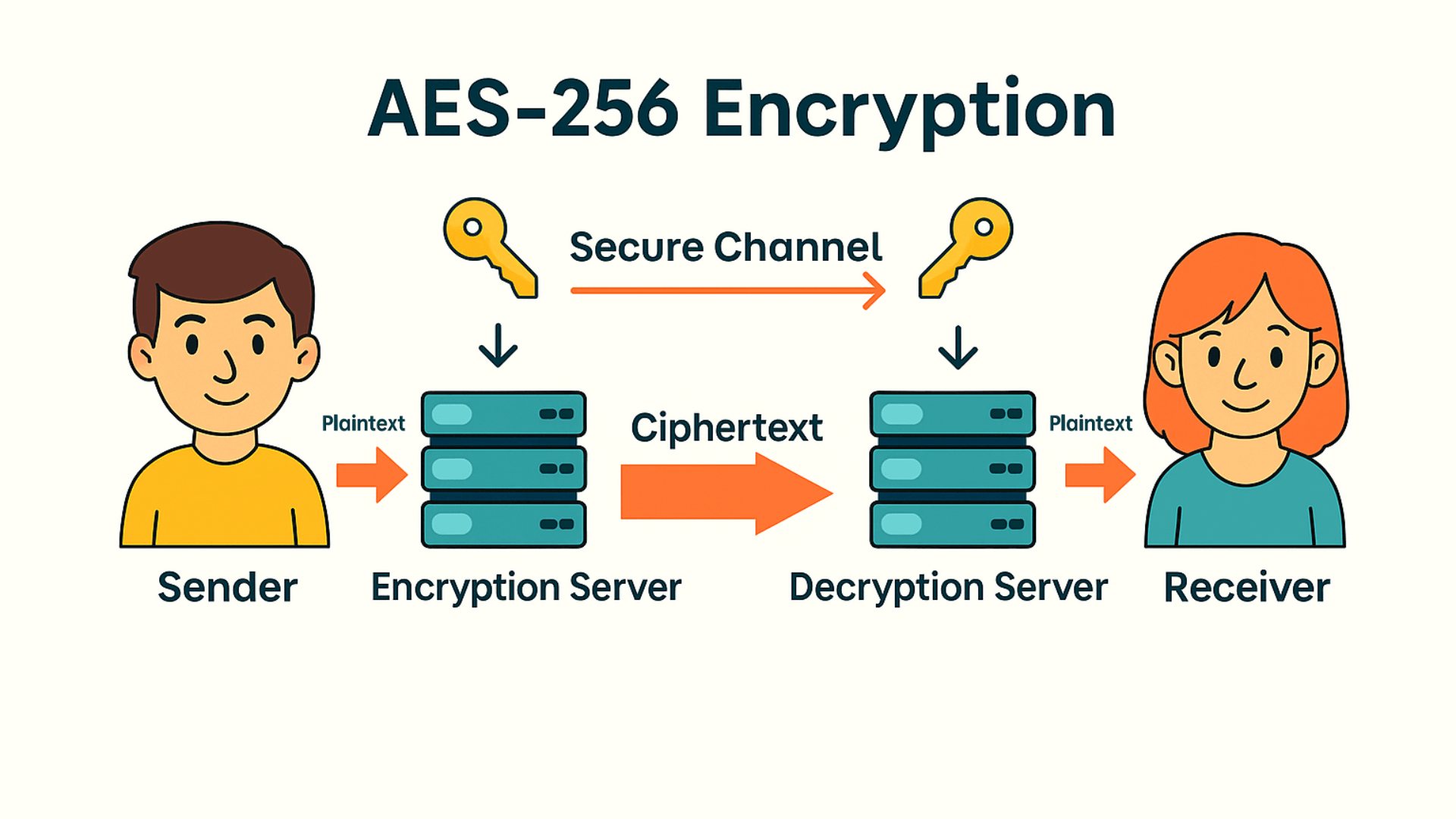
VPN encryption is often the heart of a VPN service. When you perform any online activity, the VPN is able to transform the data packets transmitted during the process into unreadable ciphertext by means of an encryption algorithm, thus allowing only those with the correct key to read the useful info.
NordVPN uses the strongest level of encryption algorithm available – AES-256 (Advanced Encryption Standard, 256-bit). Not only is it the encryption tech trusted by banks, governments, and the military, but it also comes standard in all high-quality VPN products these days. Even a top hacker would have to take a supercomputer an astronomical amount of time to try to break AES-256 violently. Therefore, NordVPN’s security foundation is solid.
VPN Protocols
Besides the encryption algorithm, the VPN protocol is also an important part of VPN encryption – it’s like the routes and modes of transportation that data chooses when traveling through a VPN tunnel. This also means that the speed and security of a VPN will vary depending on the protocol. Therefore, which VPN protocols are offered is also an important factor in evaluating whether a VPN is secure or not.
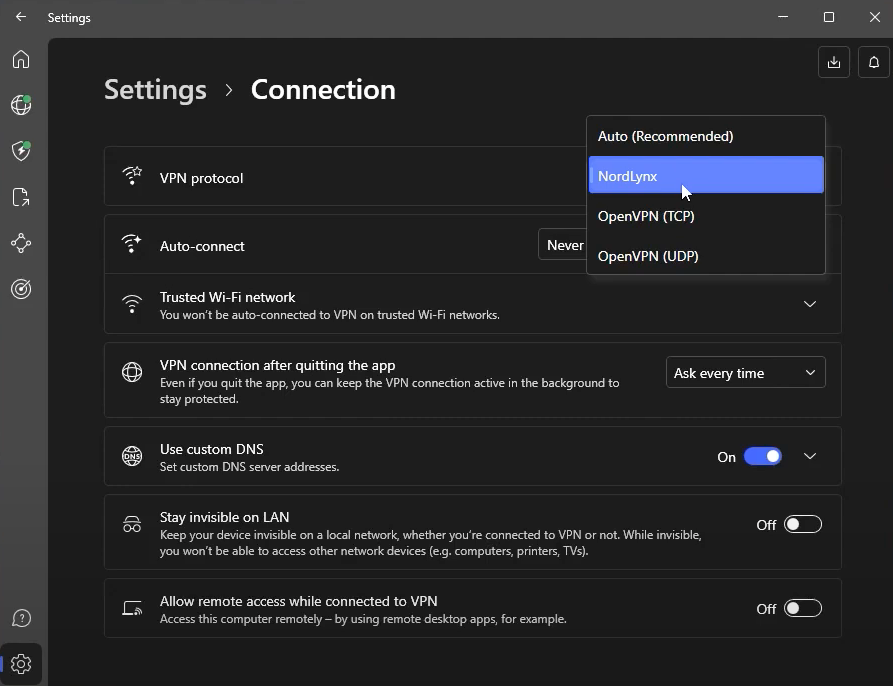
Currently, NordVPN offers three main protocols for users to choose from:
- OpenVPN: The classic open-source protocol with excellent security and stability. NordVPN offers specific versions for both TCP and UDP ports.
- NordLynx: NordVPN’s own protocol, based on WireGuard, which offers great speeds without compromising on security.
- NordWhisper: NordVPN’s newest protocol that helps users deal with filtered content. (This protocol is currently not supported on macOS, so it’s not shown in the screenshot.)
The scenarios for the above three protocols may vary depending on the customer’s needs, but all of them do have a solid enough security foundation.
Security Features
After confirming that NordVPN has a solid encryption underpinning, I tested the security features it offers to see if it can really bring further privacy to users in a complex and changing network environment.
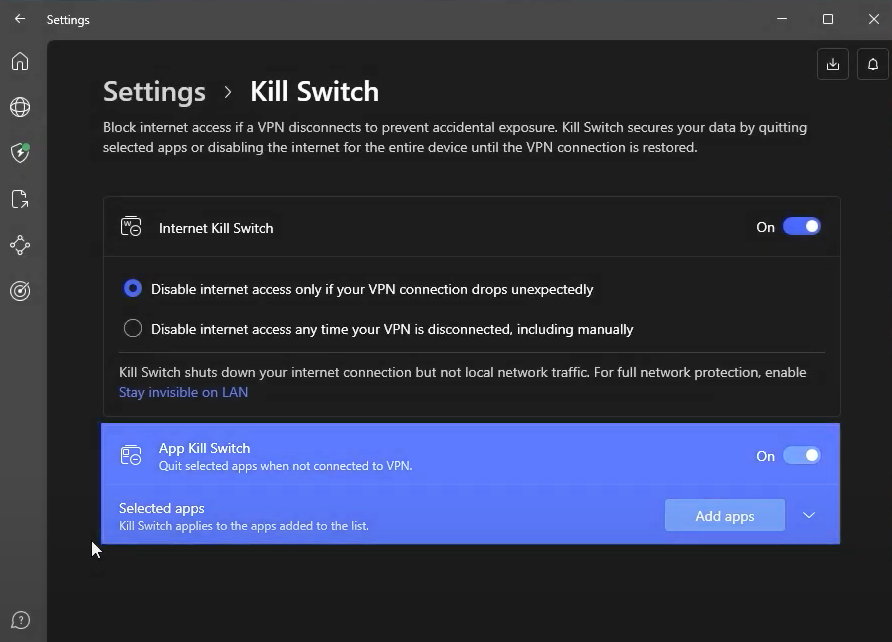
Kill Switch
Kill Switch is one of the most basic and critical security defenses for VPN users. When a VPN connection is accidentally disconnected, it immediately blocks the device from accessing the Internet, preventing the real IP address and sensitive data from being exposed at the moment.
In my test, I simulated disconnecting the VPN connection on my Mac, and Kill Switch cut off the network almost simultaneously – the response was fast and stable. It’s also worth noting that NordVPN offers a more flexible App Kill Switch mode: instead of disconnecting directly, it closes specific apps you’ve preset, such as Chrome. This design preserves more freedom while protecting privacy.
Split Tunneling
Split Tunneling allows users to choose which apps go through a VPN tunnel and which connect directly to the Internet. While it may seem like a convenience feature at first glance, it’s actually a more granular means of control from a privacy standpoint – allowing you to focus on protecting critical data streams without interrupting efficiency.
For the test, I set up my browser to connect to a VPN to access online banking while streaming 4K content on Disney+. The results showed that the encryption-affected speed drop did not spill over into streaming playback, and the experience was smooth.
Double VPN
Double VPN encrypts and forwards your online traffic via two VPN servers in sequence. This means that even if the first connection is cracked and monitored by an attacker, the extra layer of security provided by Double VPN makes it impossible for anyone else to know your true location or destination.
Before testing this feature, I was actually a bit worried about the impact on internet speeds, but in practice, I could barely feel any noticeable speed loss, proving that NordVPN has done a good job of optimization.
The Test Result of NordVPN Leak Protection
In addition to experiencing NordVPN’s security protection, I also conducted a data leakage test using ipleak.net, dnsleaktest.com, and browserleaks.com to verify that NordVPN is actually working.
The test results showed that my IP address was switched to the server address when using NordVPN, and the DNS and WebRTC test results were all clean.
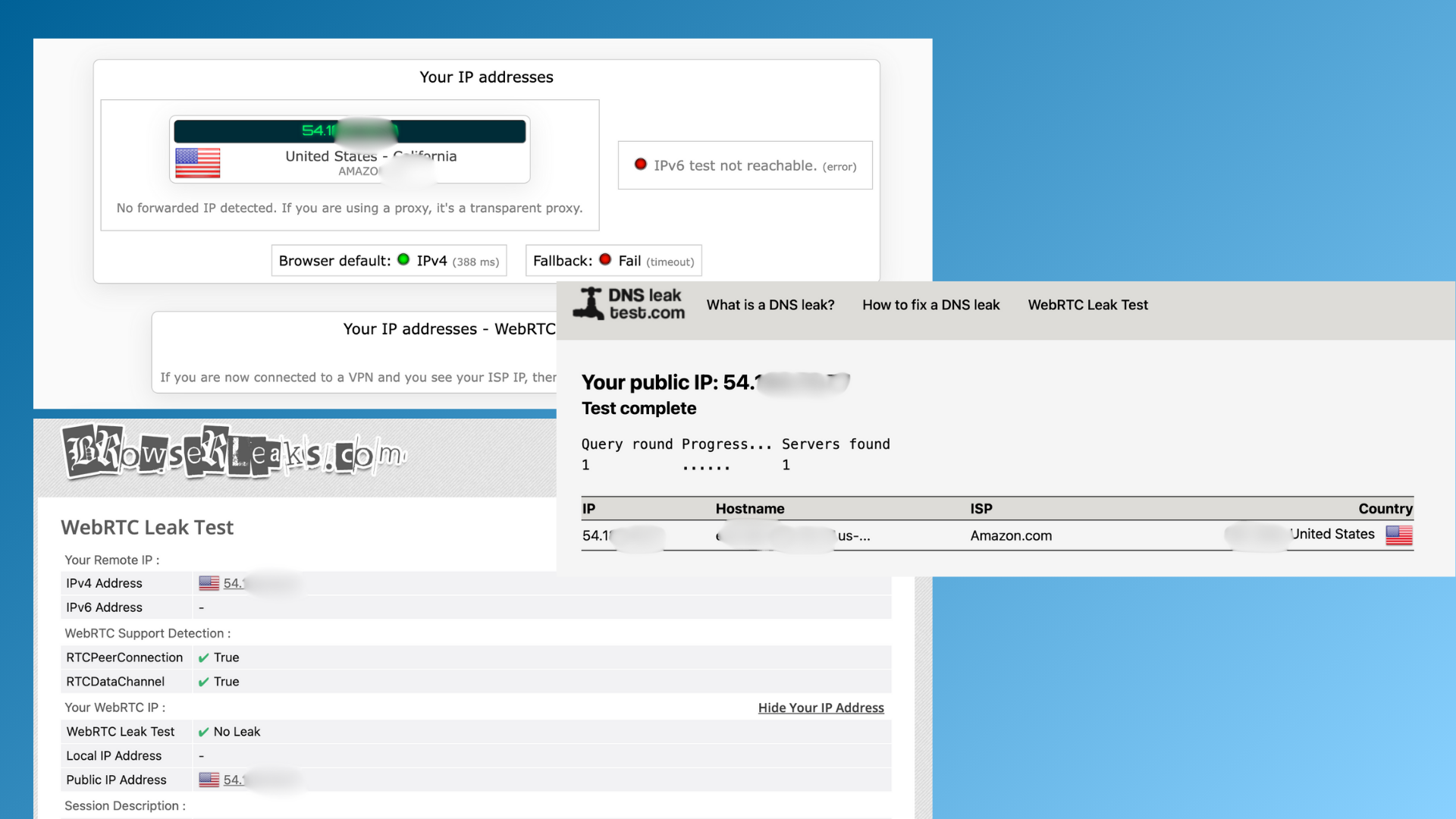
The IP Address/DNS/WebRTC Leak Test Results of NordVPN
Additional Online Protections
In addition to the encryption algorithm and core security features, NordVPN comes with some useful additional protection tools that may not be as “obvious” as Kill Switch, but can sometimes play a key role in combating broader cyber threats.
Dark Web Monitoring
Personal digital identity breaches have become very common in recent years. Once your data is collected by a third party and trafficked to shady merchants or the dark web, you will experience unpredictable and serious consequences.
The Dark Web Monitor provided by NordVPN can alert you when your info appears on the dark web. While this kind of alerting won’t stop the leak itself, it can help you “stop the bleeding” by changing your passwords or enabling stronger protection before the risk grows.
Threat Protection Pro
Threat Protection Pro is NordVPN’s built-in antivirus tool that automatically blocks ads, trackers, and prevents you from encountering malware and phishing links. It’s also independent of the VPN service, meaning that it works silently in a background process even when you’re not connected to the VPN.
I visited a couple of well-known ad-hit sites and tried to download some sample files for testing purposes, and NordVPN accurately blocked them. While it’s not a replacement for specialized security software, it’s more than enough for most casual users to deal with everyday risks.
Note that Threat Protection Pro is currently only available for Windows and macOS devices, while other platforms only support a simplified version named Threat Protection.
Multi-factor Authentication
Beyond helping you prevent external threats, NordVPN also offers MFA to help you secure your account. I let my colleague, who is far away, log into my NordVPN account using her device with MFA turned on, and the system instantly triggered the verification. This also means that even if my password is known to an attacker one day, he won’t be able to log into my account easily.
From the core encryption, security features, and additional tools, NordVPN did show me that a mature VPN service provider has considered all aspects of online security protection. But the thing is, technical prowess alone is not enough. After all, the VPN itself is a “third party” to us – not only can it encrypt our traffic, but it can theoretically see everything we do online. So trust is not just about technology, it’s about commitment and transparency.
Privacy Policy and External Audits
Next, it’s time to talk about NordVPN’s privacy policy and external security audit to see if it deserves the “trustworthy” label.
No-Log Policy
In the Internet environment, Log usually refers to data that records user or system activity. And the reasons why VPN services create logs usually include performance testing, security monitoring, troubleshooting, feature access, and even compliance requirements.
However, these logs may involve sensitive info about users, and thus are highly susceptible to concerns about privacy breaches. This is the fundamental reason why most VPN providers choose to implement a No-log Policy to assure users that their privacy will not be violated. However, it is important to note that keeping no logs is not that easy. There are strict laws in many countries and regions that require companies to store user data for at least a certain period of time.
NordVPN, which operates out of Panama – a country that does not have strict data retention laws – effectively circumvents this restriction. The provider states that they enforce a strict No-Log Policy and do not store personal data such as users’ IP addresses, bandwidth usage, device info, browsing history, downloaded software, and used apps, allowing users to enjoy streaming media, online gaming, and other services with greater freedom.
RAM-based Servers
Of course, as normal users, we seem to be tired of the empty promises made by some providers. The No-log policy would be meaningless if it weren’t backed up by actual facilities. And in my research, I found that NordVPN does have the backbone to make promises – they use RAM-based Servers.
RAM-based Servers are special servers with volatile memory. Whenever the server shuts down, the data stored and processed in the server will be erased. This also means that users no longer have to worry about the risk of data leakage when using NordVPN. Even in the case of hardware problems, personal data stored on RAM-based Servers will be deleted when the power goes off, preventing unauthorized third parties from accessing and stealing it. This not only reduces the security risk, but also gives NordVPN’s no-log promise real technical backing.
Third-Party Audits
It’s easy for a VPN provider to say it’s “ no-log”, but that statement is only credible if it’s been subjected to an independent third-party security audit. According to my findings, NordVPN has done an excellent job in this regard.
NordVPN has completed five independent No-Log audits to date, the latest of which was made public on February 11, 2025. The assessment was conducted by auditor Deloitte Audit Lithuania. In line with the results of the previous four, this independent audit continues to confirm that NordVPN’s protection of user privacy is indeed not a paper exercise.
2018 Security Incident of NordVPN
NordVPN is not without its faults. As recently as 2018, the provider was involved in a security incident where its servers in Finland were accessed without authorization. However, benefiting from its strict No-log policy, this security incident didn’t have a serious negative impact. And to prevent such incidents from happening again, NordVPN has taken a number of improvements and refined its internal security audits – enabling RAM-based Servers is a part of that.
From the choice of its legal jurisdiction and the design of its physical infrastructure to regular audits by independent third parties, NordVPN has made a sincere effort to build a “trust mechanism”. It not only promises “no-log” but also makes it a reality through multiple layers.
The Final Answer: Is NordVPN Safe?
After a few days of in-depth testing and thorough analysis, I think NordVPN is indeed secure. With advanced encryption technology, multiple security features, and a No-log policy practiced by RAM-based Servers, it is committed to user privacy on both the physical and security levels, and continues to validate its transparency and trustworthiness through third-party audits.
And honestly, I don’t think NordVPN is perfect for full security. VPN encryption does reduce the likelihood of your private data being compromised, but it doesn’t prevent you from being exposed to malicious viruses, phishing links, identity theft, and other online threats. Even though NordVPN also offers additional security services like Threat Protection Pro, it still has room for optimization compared to professional antivirus software.
But overall, for the vast majority of users concerned about privacy and security, NordVPN is one of the most trustworthy VPN options on the market today. In other words, if you’re looking for a secure VPN provider to enable you to gain more freedom online, then NordVPN can indeed be included in the list of options.
The Bottom Line
This is my complete review of NordVPN security. Is NordVPN safe? My answer is yes. But it’s important to note that using NordVPN doesn’t guarantee that you’ll be 100% safe from any online risks. It’s important to develop good online habits, learn more about data protection tips, and remain sensitive to your privacy to make safe browsing easier!




